In an era where personal information is constantly harvested, protecting one’s privacy has become a pressing concern. Each day, countless individuals find themselves grappling with the ramifications of having their data collected without consent. This feeling of vulnerability is widespread, as many wonder how to regain control over their digital identities. Fortunately, numerous innovative options exist that empower users to reclaim their privacy.
Many people are unaware of the extent to which their personal details circulate online. From basic contact information to intricate behavioral patterns, this data is often exploited without any regard for individual rights. However, there are practical measures available that can significantly help individuals mitigate these invasions of their personal space. By leveraging modern advancements, anyone can take proactive steps to safeguard their information.
Whether it’s through user-friendly platforms or specialized services, the ability to manage one’s online footprint is more accessible than ever. This new landscape offers a variety of methods to minimize intrusive practices. With just a few clicks or taps, individuals can initiate the process of enhancing their privacy settings. The significance of these actions cannot be overstated, as they allow users not only to protect themselves but also to regain a sense of agency over their own lives.
As more people become aware of the threats posed by unchecked data collection, the demand for effective privacy solutions has skyrocketed. Options abound, catering to different needs and preferences. From comprehensive software to intuitive mobile functionalities, the array of available resources is truly impressive. Embracing these innovations can transform how individuals interact with their private information.
Understanding Data Brokers
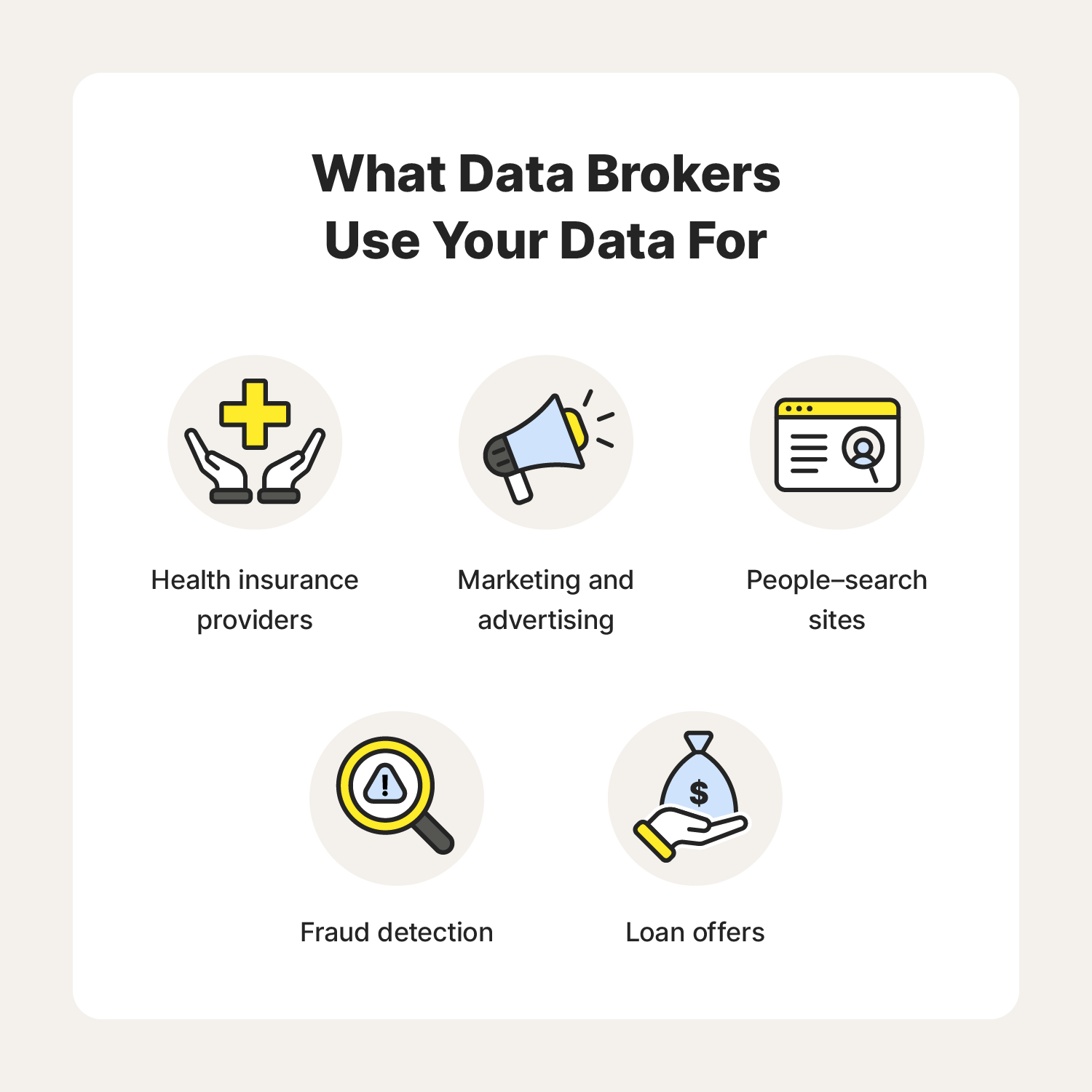
In today's digital landscape, a complex web of entities operates behind the scenes, collecting and exchanging personal information. These businesses play a pivotal role in the ecosystem of privacy and security. They gather details from various sources, often without our explicit awareness, creating a detailed profile of individuals. As technology evolves, so does the sophistication of these practices. The implications of this activity are profound.
At their core, these organizations are intermediaries, facilitating the collection and sale of personal information. They utilize various channels to acquire data, from public records to online activity. This information can often be pieced together to form a comprehensive view of an individual.
Many consumers are unaware of how prevalent this practice has become. For instance, a simple online search can yield a goldmine of information about you. This data can include your purchasing habits, interests, and even your location. The range of information collected is staggering; it might involve details as innocuous as your favorite hobbies or as sensitive as your financial history.
On one hand, this commercial activity can lead to more personalized services and tailored offers. On the other, the lack of transparency raises significant concerns. If you consider how readily available personal data has become, it is alarming to think about who has access to it and how they might use it.
Understanding these entities requires awareness of their methods and intentions. They thrive on the assumption that most users are oblivious to their existence. Without vigilance, individuals could unknowingly allow their information to be exploited, often leading to unwanted solicitations or even identity theft.
Risks of Data Broker Involvement
In today's digital landscape, the presence of information aggregators poses significant challenges to personal privacy. These entities collect and sell vast amounts of consumer information, often without individuals' consent. This practice raises serious concerns about how personal data is handled and the potential consequences of such actions. Individuals may not fully grasp the implications of having their information shared far and wide. The delicate nature of personal data makes it an attractive target, and as such, it is crucial to understand the risks associated with this involvement.
Information sellers can expose sensitive details to various third parties. This includes marketers, advertisers, and even malicious actors, all of whom may misuse the information for their gain. Many people remain unaware of how their data is being utilized. Moreover, the anonymity provided by technology complicates accountability. As a result, individuals are left vulnerable in a system they cannot easily navigate.
One major concern is identity theft, which can have devastating effects on one's financial health. When personal details are easily accessible, it's much easier for fraudsters to impersonate someone else. This can lead to unauthorized transactions, damaged credit scores, and even legal troubles for the victim. Additionally, sensitive information can be used to manipulate individuals, leading to targeted scams and phishing attempts.
Furthermore, the sale of personal data can result in unwanted marketing tactics, bombarding individuals with advertisements based on their behaviors and preferences. The constant influx of targeted ads can be overwhelming, leading to a frustrating online experience. Privacy violations do not only stop at commercials, though; they can also create a chilling effect, where individuals self-censor their online activities due to fear of being monitored or profiled.
Long-term exposure to these risks may erode trust in digital platforms. Consumers might begin to question the integrity of online services. As they feel increasingly exploited, people may even choose to withdraw from certain services altogether. This growing awareness underscores the urgent need for education regarding personal data management and protection measures. Thus, understanding these potential dangers becomes essential for anyone navigating the modern digital age.
Risks of Data Broker Involvement
The presence of intermediaries in the information marketplace poses several challenges for individuals. These third-party entities collect, aggregate, and sell personal information to businesses and organizations. This practice can lead to various adverse effects on privacy and security. Moreover, many people remain unaware of the extent to which their information is being utilized. The risks are not confined to mere data misuse; they extend into numerous aspects of daily life.
One significant danger is identity theft. This occurs when someone illegally acquires personal details to impersonate another person. Financial fraud can ensue, resulting in severe emotional and financial repercussions. Victims often face long battles to reclaim their good name. In addition, the stress of such situations can affect their mental health. Data brokers often lack robust security measures, making the information they collect vulnerable to breaches.
Another alarming concern is the potential for discrimination. Information about individuals can be used to create profiles that lead to biased decisions in hiring, lending, and other areas. Such practices can perpetuate societal inequalities and further marginalize vulnerable groups. This not only harms individuals but can also damage the reputation of companies engaging in such practices. As algorithms increasingly dictate outcomes in our lives, the implications are vast and far-reaching.
The commodification of personal information also encourages a culture of surveillance. Constant monitoring by corporations makes people feel uneasy. This pervasive sense of being watched can stifle authenticity and freedom of expression. In a world where privacy is continually eroded, many individuals may choose to self-censor their thoughts and actions, ultimately compromising their personal autonomy.
Moreover, the lack of transparency surrounding these practices complicates matters further. Many individuals do not know where their information is going or how it will be used. This ignorance can lead to feelings of helplessness, as people grapple with the consequences of decisions made without their consent. Without clear regulations, the industry operates in a gray area where accountability is often absent.
Lastly, the aggregation of personal data can lead to unwanted targeting. Advertisements tailored to previous actions may seem harmless, but they can invade personal space and create discomfort. Over time, this ongoing influence can reshape choices and preferences, subtly nudging individuals toward specific products or services. Such manipulation raises ethical questions about consent and individual agency.
How Your Data Is Sold
The process of selling personal information is intricate and often hidden from the average user. Individuals may unknowingly have their private details packaged and traded without consent. This market thrives on the vast amounts of data generated daily. Most people remain unaware of how their information circulates beyond their control.
Typically, the cycle begins with data collection. Companies gather information from various sources, including:
- Online activities via social media platforms
- Purchases made in stores and online
- Public records and government databases
- Surveys and questionnaires
Once obtained, this data is compiled, analyzed, and categorized into specific profiles. Such profiles can reveal insights about your habits, preferences, and even clean up your online data financial situation. These pieces of information are then sold to marketers, advertisers, and other businesses that are eager to target potential customers more effectively.
Moreover, this transaction often happens in bulk. A company may not sell individual data points; instead, they offer aggregated data, which paints a broader picture of consumer behavior. This approach, while seemingly innocuous, raises significant concerns about privacy and consent.
Additionally, the types of businesses that purchase these data sets are varied. Retailers, insurance companies, and even political organizations utilize this information for tailored marketing campaigns. They aim to increase their sales or influence decisions based on the understanding they gain from that data. Individuals' preferences and behaviors become valuable commodities in a competitive market.
In essence, personal data becomes a product, traded amongst several parties in exchange for profit. This phenomenon highlights the need for awareness about what is happening behind the scenes. Understanding this process is crucial for anyone concerned about their information being used without their knowledge or permission.
Methods for Opting Out
In today’s digital landscape, many individuals seek ways to safeguard their personal information. The majority of people are unaware of how extensively their details are collected and utilized. When one becomes informed, protecting oneself from intrusive practices becomes a priority. There are several avenues available to regain control. This section delves into the various strategies for minimizing personal exposure.
One fundamental approach is the use of online privacy resources. These options help individuals manage their information proactively. For instance, various websites provide guidance on how to remove personal details from public databases. Many users find comfort in understanding these processes, which can often feel daunting. It is crucial to stay vigilant and aware of your digital footprint.
Additionally, individuals can request the deletion of their records from specific platforms. Services often have clear policies and straightforward methods for individuals to follow. However, compliance with such requests may not always be guaranteed. Nevertheless, persistence is key; if users don't see results right away, revisiting the request periodically can yield better outcomes.
Furthermore, regular monitoring of your online presence can be enlightening. Searching for your own name and associated information can reveal surprising results. Many people discover that their data is more accessible than they initially thought. Keeping track of what information is available can inform more effective privacy practices. This might encourage users to take further steps in data management.
| Action | Description |
|---|---|
| Website Removal Requests | Contact specific sites to have your information deleted. |
| Privacy Monitoring | Search for your name online to check data exposure. |
| Regular Updates | Revisit privacy settings frequently to ensure they meet your standards. |
Moreover, it’s beneficial to adopt privacy-conscious habits. Using more secure platforms for communication is a good start. Many users overlook the risks associated with popular social media channels. By exploring alternatives that prioritize confidentiality, individuals can enjoy a safer online experience. Thus, choosing to interact with more secure services can significantly reduce unwanted data sharing.
In conclusion, taking steps to limit personal information exposure is achievable. With a variety of methods available, everyone can play an active role in minimizing their digital footprint. Awareness is vital, alongside a proactive approach in managing one's online information. Although the process may seem arduous at times, the peace of mind gained is invaluable in today's interconnected world.
Technology Solutions for Privacy
In today’s digital age, safeguarding personal information is more crucial than ever. Many individuals are unaware of the extent to which their details can be collected and sold. Thankfully, a variety of innovative solutions exist to enhance user privacy. These approaches are designed to empower individuals to regain control over their information. They offer the promise of a more secure online experience while minimizing unwanted exposure.
Several applications are specifically created to enhance privacy. They help protect against intrusive tracking practices. One popular type of software is a privacy-focused browser extension. These extensions block unwanted ads and trackers that follow users across the web. By limiting the data that websites can collect, they contribute to a more private browsing experience.
Moreover, password managers play an essential role in enhancing online security. They generate strong, unique passwords for each account, reducing the risks associated with data breaches. When one password is compromised, others remain secure. This prevents unauthorized access to sensitive information and ensures that users maintain better oversight of their digital credentials.
Another effective resource for maintaining confidentiality online is the use of encrypted messaging applications. These apps enable users to communicate without the fear of interception. Unlike traditional messaging services, they ensure that conversations remain private and secure. Encrypted messages can only be read by intended recipients, adding an extra layer of protection.
Virtual Private Networks (VPNs) also serve as invaluable assets for anyone concerned about privacy. They create a secure connection between a user’s device and the internet, masking the user’s IP address. This makes it significantly more challenging for third parties to trace online activities back to an individual. By encrypting internet traffic, VPNs provide an added safety net against data harvesting.
In conclusion, a range of effective solutions exists to protect personal information in today's interconnected world. Users can take concrete steps to bolster their online security. Whether through dedicated software, encrypted communication channels, or secure internet connections, the tools available can significantly reduce the risks associated with online exposure. Prioritizing privacy is not merely a choice; it’s a necessity for anyone navigating the digital landscape.
Using VPNs and Secure Services
In today’s digital world, maintaining privacy is more crucial than ever. With the rise of online threats, ensuring personal information remains confidential has become a priority for many users. Various solutions exist to bolster security and safeguard sensitive data. Virtual Private Networks (VPNs) serve as a primary line of defense.
A VPN creates an encrypted tunnel between your device and the internet. This makes your online activities more difficult to monitor. By masking your IP address, it also grants you anonymity. Additionally, a trustworthy VPN can protect you from hackers and malicious attempts to access your data.
Besides VPNs, employing secure services can significantly enhance your privacy. Solutions like encrypted messaging applications prevent unauthorized access to your conversations. These platforms ensure that only the intended recipient can read your messages. Furthermore, utilizing cloud services that prioritize encryption adds an extra layer of security to the files you store online.
When searching for a VPN or a secure service, transparency is vital. Look for providers that clearly outline their privacy policies. Avoid options that keep extensive logs of user activity. Instead, prioritize those that offer no-log policies, ensuring that your digital footprint remains minimal.
Moreover, consider the jurisdiction under which these services operate. A company based in a privacy-friendly country is often a safer choice than one located in regions with invasive data retention laws. These factors contribute significantly to the level of protection you receive.
Ultimately, combining multiple security measures leads to a more robust defense against potential threats. Using a reputable VPN alongside encrypted applications creates an effective shield for your personal information. In an age where privacy concerns are mounting, taking proactive steps can help preserve your digital freedom.
Using VPNs and Secure Services
In today's digital landscape, protecting one's privacy has become essential. With the constant exchange of information online, individuals must be proactive. Various methods exist to safeguard personal data from potential threats. Utilizing secure connections can be a powerful step in maintaining confidentiality. Anonymity is not just a luxury; it is a necessity.
Virtual Private Networks (VPNs) offer a shield against unwanted surveillance. They encrypt internet traffic, making it difficult for anyone to monitor online activities. Furthermore, secure connections prevent hackers from accessing sensitive information. Many users turn to these services for enhanced safety. However, not all VPNs are created equal; some prioritize user privacy better than others.
When selecting a VPN, one should consider several factors. Speed, encryption protocols, and logging policies are critical. A reliable VPN service should ideally have a no-logs policy, meaning it does not store user activity. Additionally, look for services that offer robust encryption. This ensures that data remains secure during transmission.
Moreover, secure services extend beyond VPNs. Encrypted messaging applications, for instance, provide a layer of confidentiality. They protect conversations from eavesdroppers, ensuring personal discussions remain private. Email encryption tools offer similar benefits, safeguarding sensitive correspondence. Using these applications helps maintain a secure digital environment.
However, it's vital to remain vigilant and informed. While secure services enhance privacy, users must practice good digital hygiene. Regularly updating software, using strong passwords, and being cautious of suspicious links are all recommended practices. Combining secure services with prudent behavior creates a formidable defense against breaches.
| Service Type | Key Features | Recommended Options |
|---|---|---|
| VPN | Encryption, no-logs policy, multiple server locations | ExpressVPN, NordVPN |
| Encrypted Messaging | End-to-end encryption, self-destructing messages | Signal, WhatsApp |
| Email Encryption | Secure communication, protection against phishing | ProtonMail, Tutanota |
Ultimately, the combination of VPNs and other secure resources plays a vital role in personal data protection. Being proactive about online privacy is more crucial than ever in this interconnected world. Individuals should feel empowered to take control of their digital footprint. By employing these strategies, anyone can work towards a more secure online existence.
Legal Rights and Data Protection
Understanding the rights consumers hold in relation to their personal information is crucial. Each individual navigates a complex landscape of privacy laws that can vary widely. These regulations are designed to safeguard individuals against misuse of their private details. Knowledge empowers you. It helps you take control of your information.
In many jurisdictions, individuals are granted specific entitlements that ensure their privacy is respected. For instance, the right to access personal data allows individuals to request information held about them. Additionally, there are provisions for rectifying inaccurate details, which is essential for maintaining correct records. This is particularly important if your data is used in ways you didn’t consent to.
Another significant aspect is the right to delete personal information. If the data is no longer needed or if it was collected unlawfully, you can request its removal. This right is often referred to as the right to be forgotten. However, exercising this right can be complicated, depending on the applicable laws in your region and the policies of the companies involved.
Moreover, there are regulations that require businesses to be transparent about how they collect and use data. Citizens deserve to know what personal information is being shared and with whom. This is essential for informed consent. If a company fails to comply, they may face serious penalties. In some instances, individuals may also be entitled to compensation for the misuse of their data.
Various organizations advocate for consumer rights. These groups provide resources and support to help individuals understand their protections. They often offer legal guidance and can assist in navigating disputes with corporations over data privacy issues. Staying informed is vital, as laws are constantly evolving and changing.
Ultimately, awareness of one’s rights can significantly enhance personal security. By actively engaging with the available resources, you can better protect your identity in an increasingly interconnected world. Remember, your information is valuable, and you have the power to manage it effectively.
Resources for Further Assistance
When navigating the complexities of personal information management, having the right resources can be invaluable. Many individuals feel overwhelmed by the sheer volume of information available. However, there are several key organizations and websites that can offer guidance. These resources can help you understand your rights and provide strategies for safeguarding your privacy. In addition, they can assist with practical steps to take in the digital landscape.
Firstly, government agencies often provide crucial information. They outline the legal frameworks surrounding data protection. This ensures that citizens are informed about their rights and the measures they can take. Websites like the Federal Trade Commission (FTC) and the General Data Protection Regulation (GDPR) portal are excellent starting points. They encompass a wide array of topics and can answer many common questions.
Non-profit organizations also play a significant role in educating the public. Groups like Electronic Frontier Foundation (EFF) and Privacy Rights Clearinghouse focus on various aspects of privacy advocacy. They produce comprehensive guides and have dedicated hotlines. These resources have been instrumental in helping individuals reclaim control over their personal information. Using them can significantly improve your understanding of privacy issues.
| Organization | Website | Focus Area |
|---|---|---|
| Federal Trade Commission (FTC) | www.ftc.gov | Consumer protection and privacy rights |
| Electronic Frontier Foundation (EFF) | www.eff.org | Digital privacy advocacy |
| Privacy Rights Clearinghouse | www.privacyrights.org | Personal data management |
| General Data Protection Regulation (GDPR) | gdpr.eu | European data protection standards |
Supportive communities can also be a great asset. Online forums and social media groups often share personal experiences. These spaces foster discussion about privacy strategies and provide collective advice. Participating in these communities allows individuals to learn from each other. It helps build a sense of solidarity in the journey toward better privacy practices.
An array of privacy-focused blogs and newsletters can also keep you informed. Subscribing to updates from these sources can be quite beneficial. They often cover the latest trends and changes in the digital privacy sector. Furthermore, staying updated allows you to adjust your strategies accordingly. Knowledge is power, especially when it comes to your personal information.
In conclusion, there is a wealth of resources available for anyone seeking to enhance their understanding. From government websites to non-profit organizations, the options are abundant. By leveraging these materials, you are taking proactive steps to ensure your privacy. Whether you are looking for legal information or community support, the right resources can make all the difference.
